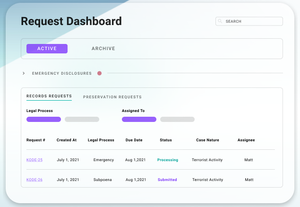
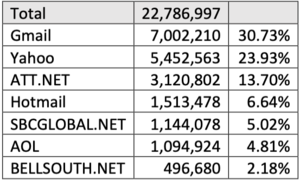
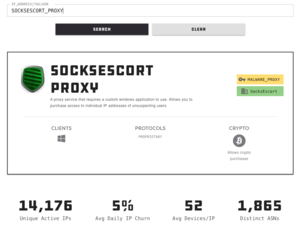
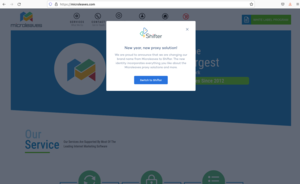
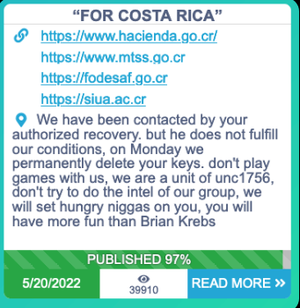
About 11,515 results found.
(Query 0.07400 seconds)
- All
- Images

Using gazes for effective tutoring with social robots
cywzf65ws6k6nd6rr5dwmbuwg7bcf6wx3ukub62g2nhannsjoskq.b32.i2p

Travis Barker Hospitalized for Pancreatitis
y5edab4637s2zmqhxr2o7v4oc4p3pwg3vtkpwmqsutjiuunvfs5q.b32.i2p

Woman writing social media posts on laptop.
y5edab4637s2zmqhxr2o7v4oc4p3pwg3vtkpwmqsutjiuunvfs5q.b32.i2p

We recently found that some email addresses and phone numbers provided for account security may have been used unintentionally for advertising purposes. This is no longer happening and we wanted to give you more clarity around the situation:
bentasker.i2p

A view from behind of a group of people standing and overlooking the Hong Kong skyline at night. The people hold with their phones high with the flashlight turned on.
themarkup.i2p

Towards having your privacy and security and exchanging crypto too
cywzf65ws6k6nd6rr5dwmbuwg7bcf6wx3ukub62g2nhannsjoskq.b32.i2p

Answering machine - yes I should really have pointed the speech bubble at the speaker.
bentasker.i2p

A book on loss of a spouse, a bloody pig mask and hustler: barely legal. All items sent as part of the harassment campaign
bentasker.i2p

As you may remember, at least one of these stalkers leaves near daily explicit and graphic death threats in my voicemail.
bentasker.i2p

Exploring an Attack on Image Scaling Algorithms
vemrh76ebiisqqhk3wmngehca4djnznnv5bd2a64qjs7pum6tu7q.b32.i2p

Pre-loading HSTS for sibling domains through this one weird trick
vemrh76ebiisqqhk3wmngehca4djnznnv5bd2a64qjs7pum6tu7q.b32.i2p

Still treating users as the enemy: entrapment and the escalating nastiness of simulated phishing campaigns
vemrh76ebiisqqhk3wmngehca4djnznnv5bd2a64qjs7pum6tu7q.b32.i2p